What you don’t know can hurt your business
Cyber risk incidents can have operational, financial, reputational, and strategic consequences for you and your customers, all of which come at significant costs. Security misconfigurations and software vulnerabilities are often the root cause of these incidents, which leave the door open for cybercriminals to exploit these weaknesses.
According to Verizon (DBIR), 82% of breaches involve the human element, misconfiguration, and misuse. Implementing the best-in-class endpoint security solution with advanced capabilities doesn’t guarantee 100% protection. A security setting within an endpoint that violates a configuration policy, or has been left insecure or misconfigured, can cause unintended behavior, putting the entire system at risk.
Common mistakes that lead to security risks !
Not keeping up with patches
Security misconfigurations
Lack of visibility into indicators of attack
Accidentally leaving unprotected endpoints
New equipment is added to the network, systems change, and patches are not applied on time – all adding to misconfiguration and creating new vulnerabilities. The more human errors present on your networks, the more chances an attacker has to access your data.
Helps to prevent and monitor cyber risk
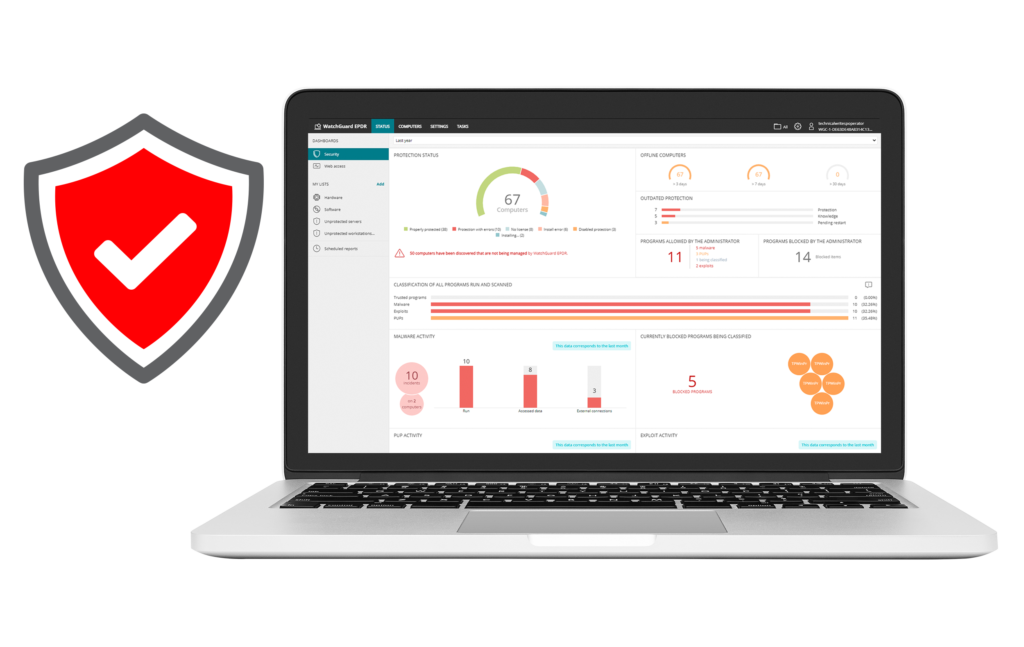
Cyber risk can have a direct impact on your systems if the endpoint solution is not properly configured. This makes existing protection measures less effective, forcing IT teams to assess their security posture continuously. So, how can risk incidents be prevented?
Security admins need to understand their cyber threat risk posture and reinforce security solution controls so they can prevent and minimize the chances of getting infected and disrupting their business. Strengthen your security posture with risk monitoring and discover vulnerabilities and security configuration weaknesses across endpoints where Viperlink Endpoint Security solutions are implemented.
Manage and monitor unprotected endpoints, indicators of attack, security misconfigurations, OS and third-party software vulnerabilities, and missing patches to proactively safeguard your network before a breach occurs.
